This is How TEWATCH protects your privacy and
data security.
Data security is the foundation of cloud communication platform. Privacy data of enterprises
and individuals must be strictly protected.
and individuals must be strictly protected.

The privacy data leak situation is grim
In recent years,the situation of privacy leaking is increasingly serious,which has brought many
troubles and data safe issues to individuals.For enterprises, once they fail to do a good job of
information protection, it will not only cause economic losses, but also damage the trust of
clients and corporate image, resulting in negative social impact. Some may even face legal
proceedings and criminal investigations. As a cloud communication platform for enterprises and
users, SUBAMIL must do its best to protect clients information and data.
troubles and data safe issues to individuals.For enterprises, once they fail to do a good job of
information protection, it will not only cause economic losses, but also damage the trust of
clients and corporate image, resulting in negative social impact. Some may even face legal
proceedings and criminal investigations. As a cloud communication platform for enterprises and
users, SUBAMIL must do its best to protect clients information and data.

Personal Privacy

Communication Data

Operating Data

Trade Secret

Business Interaction

User Portrait
TEWATCH Data encryption and Data safe
Strictly check and protect user privacy

ISO 27001 Information Security Management System Certification
 TEWATCH is ISO 27001 certified
TEWATCH is ISO 27001 certified
ISO 27001 is the globally recognised information security standards for Information Security Management Systems (ISMS). The certification shows all our hosting providers are ISO 27001 compliant. established a proper information and data protection system, ensured the management standards of cloud computing services, and can protect the information system security, intellectual property rights, business secrets of enterprises and related parties.
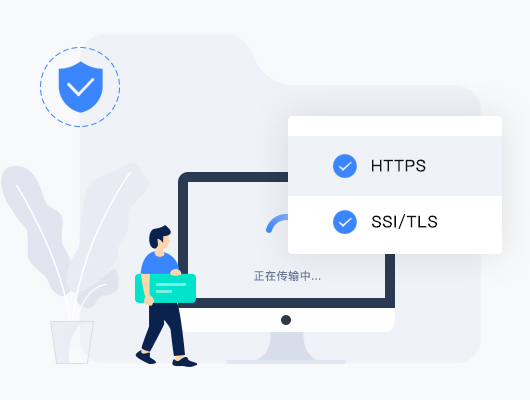
Network Protection Layer Encryption
Sources of threat:
In the process of network transmission, information and data may be stolen and hijacked. Even web pages can be tampered with directly and replaced by fake phishing websites.
Solution:
TEWATCH adopts advanced HTTPS and Sl/TLS secure encryption transmission protocol (including website, API, and Intranet transmission), layer by layer encryption, to ensure the security and stability of users.

System protection
Sources of threat:
System loophole, API interface loopholes, the lack of a complete account management system and other issues may give hackers an opportunity.
Solution:
TEWATCH prevents user data leakage through access protection, key management, patch upgrade, loophole protection, multi-account management and other multi-dimensional solutions, and truly achieves security, stability.
Real-time monitoring
Sources of threat:
If the data management in cloud communication is not transparent and detailed, there will be the risk of data leakage, which will also cause users'doubts.
Solution:
TEWATCH supports users to view account logs and export logs of data in the account at any time, and accurately to IP, time, browser and operating system.

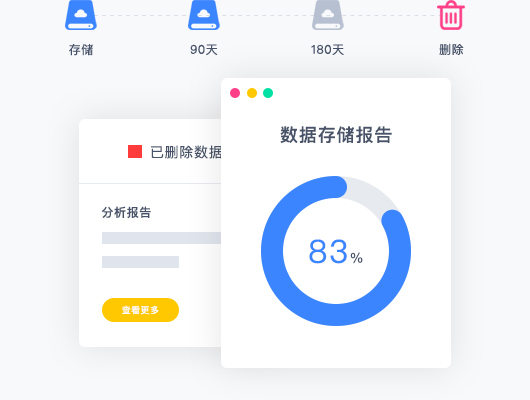
Data Storage
Sources of threat:
Data processing and storage are often neglected. Once problems such as loss, leakage and insufficient backup occur, will often lead irreversible consequences.
Solution:
In TEWATCH, all your information and data will be kept for 90 days. From 90 days to 180 days, it will enter the gray area and be ready for removal. After 180 days, all your privacy data will be permanently deleted and only the analysis report will be reserved.
TEWATCH Future Data Security Planning

Hierarchical system of authority
Reduce the complexity of authorization management, optimize the experience and improve the protection capability. Layers of checkpoints are linked to improve the multi-account management system.

Information Security Management
Continuously optimize and improve the accuracy and real-time of the log, monitor the dynamic data in detail, and form a more systematic, clear and transparent security management system.

Data Protection System
Continue to expand the scope of data protection, timely identify and solve data security risks in process control, improve risk analysis and early warning system.


